Lesson #72 - Secure Messaging with Vault Platform
Kris Durski
We are so grateful for your loyalty and support. You are the reason we do what we do. Thank you for being part of our amazing community. You rock! 👏🤟
Have you ever wondered what elements constitute secure messaging? There are quite a few messaging platforms and apps out there, that offer various levels of security and privacy in communication, such as Meta-owned WhatsApp, Signal made by Signal Technology Foundation, Swiss-made Threema, and several others. I will not be diving into their details to compare them, because they can be found in numerous publications on the Internet. My goal is to show what elements should be considered rather than making a blind choice based on the verdicts presented in those publications. Never trust security if it displays it’s secure or is advertised as secure, or worse, the most secure without giving any basis. Companies tend to advertise their products as secure rather than supporting their claim by showing what it really means. It is also important to understand that even if you “trust” your device, because it’s yours it doesn’t mean that everything on it is always secure.
Let’s look at those elements and see how they contribute to the overall security and privacy of communication. It is a common mistake to assume that if a message is encrypted then it must be secure. Putting aside for the moment the quality of encryption software or the size of an encryption key, it is important to remember that there are other factors that play key roles in secure communication. First of all, for a message to be delivered there must be metadata associated with it to allow for proper routing. That data may disclose who is communicating and with whom and that may be tracked for various purposes and jeopardize privacy, security, or even safety.
The next element to be considered is whether a messaging server has access to plaintext messages, i.e. decrypted, and thus open to potential hacking and stealing from that server. This is a model commonly known as TLS (Transport Layer Security), where a server and a device negotiate an encryption process. Although it is done with both a sender and a receiver, messages end up in plaintext on a server and that’s a big no-no. Never assume that a server is protecting your privacy and security because of some legal requirements and promises of a company that owns the service. Messages must be at least end-to-end encrypted. Here comes the most overlooked problem, which is how the messages are stored on communicating devices because they almost always are for reference in further communication. While servers are maintained by professional IT, devices usually depend on their owners and how much they know about protecting them. The reality is that vulnerabilities such as infection with malware or theft of a device may result in messages getting into the wrong hands.
Finally, the resulting element is the management of encryption keys and other information used for communication. This includes how the encryption keys are being exchanged between communicating parties, how they are being stored and accessed, and how the process of engagement is performed. Why is this element important? Well, if encryption is very hard, but access to encryption keys is not, there is virtually no protection. If the engagement process is weak, the other party may be impersonated by a hacker or a bad actor and communication may be leaked to the wrong hands, or worse, it may be the source of infection with malware. It is not that difficult to impersonate somebody on a mobile network by, for example, breaking into an unsecured SS7 protocol that connects different providers or by cloning a device of a person of interest.
The Vault Platform supports a variety of security elements that can be used to authenticate account holders, exchange secure messages, or protect and share digital and tangible assets. We’ll focus here on secure messaging between groups of individuals. A group is represented by two or more people and is usually initiated by one person who invites others to a group. I’m sure everybody understands the need for privacy and security, which if broken can sometimes even affect the person’s safety. With the growing number of applications using AI (Artificial Intelligence) the risk is even greater because, unlike people, AI can be trained with a much wider range of knowledgebase, which allows AI to detect much more context from messages than people usually do. For example, certain phrases can disclose a person’s origin or even present location.
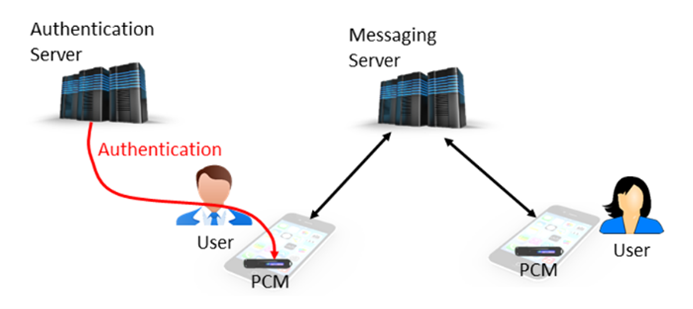
One of the key elements that distinguishes the Vault Platform is the detachment of cryptographic material from a device that uses it. Bringing that cryptographic material called PCM (Personal Cryptographic Matter) to a specific device requires authentication of its user. The description of this process can be found elsewhere so I will not be detailing it here. This feature allows for the encryption of messages in motion and in storage, not just end-to-end during the exchange. This encryption is applied regardless of the security of a physical communication channel.
Though the messages are stored encrypted, they can be transferred to another device where they can be read or edited upon authentication of a user who must be a member of the communicating group. A message can only be decrypted on a messaging app that has access to a private key, whose counterpart public key was used to seal the symmetric key that in turn encrypted the message. A stolen device or its content does not render messages as open text or disclose the true identities of members of a communicating group.
On a messaging server, users are referenced by their anonymized identifiers called tags, which are exchanged within a communicating group together with public keys. If push notifications are not used, which require the address of a device, there is no information on a server that can be used to identify or even track users. To make things more privacy and security-friendly, users can utilize different tags and encryption keys for different communicating groups and thus prevent cross-group tracking. Messages are stored on a server until they are downloaded by an app or until storage timeout.
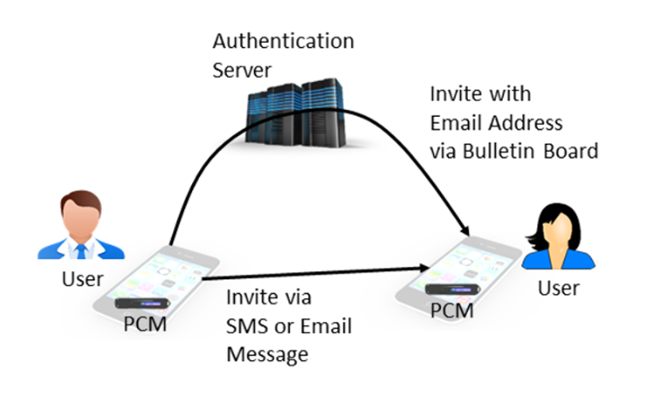
The authentication system uses emails as account identifiers because emails are usually assigned to people as global identifiers, unlike phone numbers, which can be passed to others over periods of time. Therefore engagement in a communication group is by invitation via email through a secure bulletin board on that system or special invitation messages outside the system, e.g. SMS or email. If the invited person agrees, the messaging app generates an encryption key and a randomized basis for an anonymized identifier and sends back a secure message with those components. Once the initiating app collects the information about the group, it can generate the initial message and send it to all members of a group. Members can reply to this message without making further invitations to other members. Messages do not contain emails or phone numbers, so it is up to the group what information about the members is inside, by default, it is like BCC (Blind Carbon Copy) for all members, but without any identifiable metadata.
In summary, the Vault Platform adds secure messaging on top of SDI (Secure Digital Identity) and cryptographic sharing of digital and tangible assets and uses both of them as its foundation. It addresses the requirement of permanent encryption of all messages, or in other words, end-to-end plus storage. Engagement in communication requires an invitation and secure exchange of public keys and other secrets outside the messaging system, but involving the Vault Platform for sealing them. The exchange of messages and their routing does not involve identifiable information of participants, but instead, it uses anonymized tags. Having an account on a messaging server does not provide any avenue to push a message to a potential victim and count on a mistaken acceptance or clicking on malicious content as it is on some other platforms.
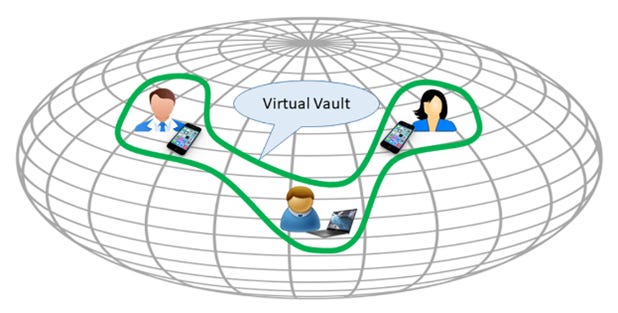
In essence, the party that creates a communication group by inviting others to become members forms a non-permeable virtual vault, which can be entered by invitation only. Messages can be backed up on any cloud file service and stay there secure while permanently encrypted and restored on any device to be available to their owner without a risk of loss if a device breaks, or unintended disclosure if it is lost or stolen.
Thank you for reading our newsletter and stay tuned for more updates from Vault Security!
It’s been a pleasure to share this article with you today. I hope you found it informative and interesting. I’ll be back next Sunday with more insights and stories. Until then, I wish you a great day and all the best.👋.