We are so grateful for your loyalty and support. You are the reason we do what we do. Thank you for being part of our amazing community. You rock! 👏🤟
In today’s digital world, one way or the other every person or institution has some confidential data exposed to the general public due to the porous nature of the entire infrastructure. With many providers when we sign up for a service or use it, we read that it is secure, or worse, the most secure. Don’t get misled by this baseless marketing buzzword. If you still use your login name and password, you are as vulnerable as you used to be. Small tricks that they apply may make things a bit more difficult for amateur hackers, but they certainly create no obstacle for hardened criminals. If you think you were not hacked, or worse, will never be hacked, because you don’t see any damage, think again.
The most value that hackers get and usually target is in data, though data is not the only reason for hacking. Data can present value when stolen or blocked from access by encryption for ransom. Thus, two key elements must be considered for protection: access to data or service by robust authentication of users and restoration of data. I don’t want to go into details about ZTA (Zero Trust Architecture), which can be found in many publications but want to show the weakness in the authentication of users and handling of access to data and their recovery.
One of the key mistakes that are being made when considering access to data or services is the belief that it is possible to hire personnel that can be fully trusted. I don’t want to say that people are in general dishonest, but people have weaknesses, and security that depends on those weaknesses is in general very weak. It only takes one weak link for the chain to be weak. Yes, you have to educate and train people and yes, you have to trust those people, but a security system has to be created in such a way that weaknesses have to have no or at most minimal effect on the robustness of the overall security. Reliance on shared secrets as verification of identity backfires sooner or later. Secrets can be either stolen, phished, or spoofed from the user or stolen even from the best-protected data center. Make no mistake, but biometrics is nothing more than a secret that can be stolen. Time-dependent tokens that require shared seed have the same problem.
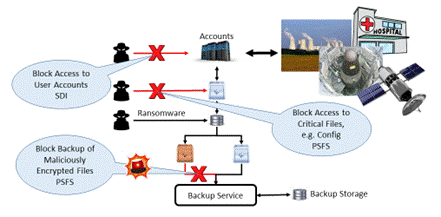
The only known technologies that do not have this flaw are based on algorithmic proof that the user who is the prover knows or has the secret without ever exchanging it with the verifier. The best-known candidates for this purpose are those that are based on PKI (Public Key Infrastructure) where the prover has the private key and the verifier has the corresponding public key. The Vault Platform has a built-in protocol called SDI (Secure Digital Identity) that relies on the exchange of encrypted/decrypted nonce where the user provides proof of having the private key by being able to decrypt a nonce generated and encrypted by the verifier. SDI provides a robust proxy to the user’s true identity thus allowing for full privacy of the user without jeopardizing the quality of proof of identity. Details can be found in other published articles available on the website.
How devastating the consequences can be if verification of identities fail? I’ll let the examples speak for themselves:
Theft of technology, e.g. blueprints of F-22 and F-35 from Lockheed Martin, which resulted in lost knowhow and more importantly introduced the threat to national security
Espionage, e.g. hacking of SolarWinds software used among others by the Federal Government, which may have enormous consequences for national security
For individuals this can result in loss of identity or property:
Loss of privacy or even life
Theft of a property such as a car
Theft of money, e.g. from a bank account or a merchant via credit card
Protection of access to data is usually obtained by setting policies based on roles that the user fulfills. This sounds like a good approach, but what happens when verification of identity fails especially if the impersonated user has administrative privileges? This happened on May 7, 2021, when an attacker using a password found on the Dark Internet was able to implant ransomware on servers that belong to Colonial Pipeline and manage the delivery of gasoline and jet fuel. The service was restored almost a week later on May 12, 2021. What if the attack was on an electrical grid or a nuclear power plant? The consequences could be much worse.
Data is not just what we can view on a browser or download, but also configuration for a nuclear reactor, a pipeline, a water dam, and many more. Modern industry is digital and connected and we all take it for granted because we have electricity, water is flowing, gas can be pumped into a car, airplanes fly in the sky, and so on. However, this infrastructure can easily disrupt our lives if identity verification fails and critical files cannot be used due to ransomware or their content is maliciously altered. Yes, the files can be backed up and restored when needed, but what if the backup was made after the files were maliciously encrypted? The answer is simple, the backup is useless until we pay ransom. What happens if the ransomware is not state-of-the-art code and the provided key upon paying the ransom does not decrypt files? I’ll leave it to imagination especially if those files were setting up nuclear reactors.
The Vault Platform provides PSFS (Portable Secure Filing System) containers, which not only protect files by encryption but also contain a structural watermark that allows for quick detection of malicious encryption. Files are backed up only if the watermark is readable, which prevents pollution of backup storage or service. This way backup is always available for quick restoration of data and configuration. In addition, files can only be accessed by authorized people or services so their content cannot be maliciously altered.
In conclusion, we’ve covered two aspects of cybersecurity: robust authentication of users with strong protection of their privacy and protection of data against intrusion and malicious encryption by ransomware.
Thank you for reading our newsletter and stay tuned for more updates from Vault Security!
It’s been a pleasure to share this article with you today. I hope you found it informative and interesting. I’ll be back next Sunday with more insights and stories. Until then, I wish you a great day and all the best.👋.